Leaving the Apple Ecosystem - part 5
Better privacy through Proton
In my last “Leaving the Apple Ecosystem” post, I wrote about my adventures with the Unplugged phone. I honestly had very high hopes for this product, and I understood that they were still a small startup, so I tried to cut them some slack. It concerned me that placing their code into open source wasn’t a high priority. But at least they finally made some progress and put the kernel on GitHub on Mar 31, 2025.
Even so, I still had many problems with how Unplugged proxies the Google app store. App updates were often delayed, or apps wouldn’t function because of dependencies on Google Play. Their customer support wasn’t great either. Sadly, Unplugged ultimately lost me as a customer.
However, even though I was disappointed with Unplugged, it led me to discover Proton, the developer of the mail, password management, and cloud storage apps that Unplugged installs on their phone. With its features and commitment to privacy, Proton quickly won me over.
Proton has been around since around 2014. In many ways, they picked up the slack in email encryption from when PGP Corporation got bought by Symantec (where software goes to die).
Proton started as a crowdfunded email app and eventually grew into a Proton AG with a well-rounded suite of apps. The non-profit Proton Foundation, based in Geneva, Switzerland, is the primary shareholder.
Proton started with an email app and then expanded to support a suite of apps that use encryption to protect your data. But Proton, unlike the iCloud suite of apps, did encryption properly. They explicitly designed their code with encryption built in by default, it can’t be turned off, and it’s not possible for them to ever have access to the data. Proton’s entire business model is based on this.
Privacy has never been part of Apple’s business model, but it should be. The need for this should be evident for any UK resident, considering how Apple capitulated to the UK’s secret backdoor request by removing iCloud encryption.
While Google’s model has been “we are going to exploit your data for advertising,” Apple’s seems to be “we are going to exploit your data for our own use.”
While writing this article, I control-clicked to bring up the “Lookup” menu, only to discover that Apple now requires location data to even to just look up a word!
Proton Mail
Proton Mail is the first app in the Proton suite I would like to talk about. I got sick and tired of Apple Mail’s occasional hangs and have been looking for a good cross-platform solution. Proton Mail integrated the OpenPGP internet standard into a secure webmail application. Later, it was ported to macOS, Windows, and Linux, as well as iOS and Android. Proton even has a Bridge app that allows you to connect with your existing email client. (see Proton download link)
Naturally, any mail sent to a recipient who hasn’t sent you a PGP key will not be encrypted, but all mail with Proton customers will be encrypted. You can also send a password-protected email to an outside recipient.
Open Source
The source code for Proton apps has been publicly available online for inspection since day one. Proton contributed to the OpenPGP implementation for JavaScript, the basis for their browser-based cryptography. They also post the audit reports publicly. (see https://proton.me/community/open-source )
Who manages the keys?
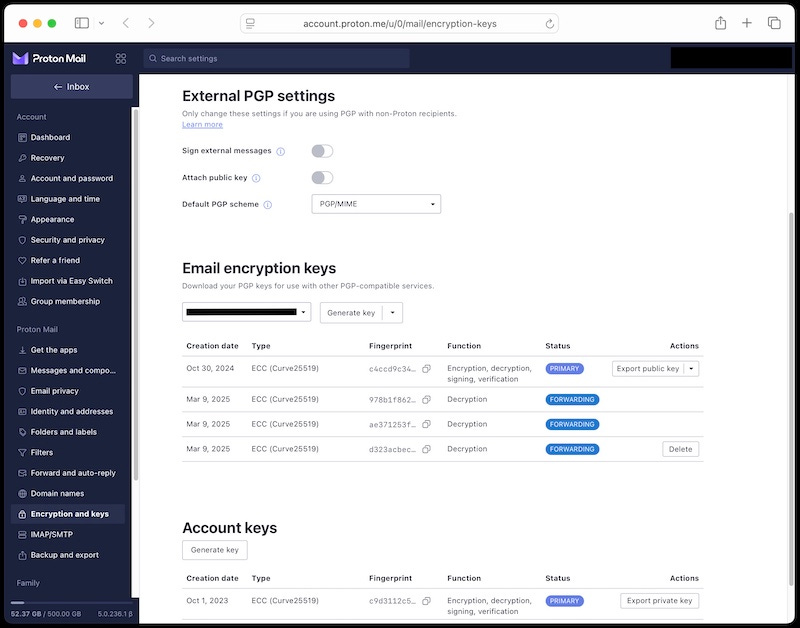
Proton has done a lot of things correctly, including addressing key management, which is one of the hardest problems related to bringing encryption to the consumer market. This problem is especially difficult for a web-based app. When you create an account, your browser generates a private key and encrypts it using your hashed password before uploading it to the server. They do not have the ability to decrypt it.
You can even examine, verify, and manage the keys from the web app.
I encourage you to dig through their blog, where you will find numerous articles about privacy. I was delighted to find that Proton supports Curve25519 Elliptic Curve Cryptography (ECC) keys.
I was also pleased to see that Proton is moving forward on something I pioneered in the early 2010s: better ways to use the blockchain to verify the authenticity of public keys. I look forward to seeing them develop this further.
Proton Pass
Proton Pass is one of the apps I use daily from the Proton suite. Proton has done a substantially better job than the Apple Keychain app. I trust it more than other commercial password apps like Enpass or 1Password. Once again, the source code is available for review, and Proton posts the results of regular security audits.
Over the years, I have used a bunch of password apps and have really come to love Proton Pass. Like most of their apps, it’s not the flash; it’s the function. I read that some users complained about problems with the autofill feature, although I have not experienced any issues with it.
Proton Drive
Next to Proton Pass, this is one of my most essential privacy apps. I use Proton Drive daily to sync and back up photos securely.
I no longer trust iCloud or Google with my data, especially because of the built-in face recognition feature. I know that Apple has claimed that all face recognition, scene, and object detection is done entirely on the device. That doesn’t mean it won’t change, and doesn’t specify any security policy on that data.
Don’t you think the face scanning part of photo apps also creates a social network map? They started doing this a decade ago with Social Mapper. And how many people advocated for the Contact Tracing scam?
One again, Proton doesn’t do this, and if they add it in the future, they will do it in a way that is not shared and again publish the code.
In addition to syncing and backing up photos, I use Proton Drive to access and securely back up documents. Think of it as Google Drive, Dropbox, or OneDrive without the hacking or personal data scanning.
Proton has even announced some of its plans to evolve this app this Spring.
Proton VPN
I personally use the Proton VPN whenever I leave my home network. I am not a VPN expert, and I chose it over the competition because I like how well the company takes security seriously and integrates with its other apps. I did find several reviews online that spoke well of Proton VPN.
Calendar and Wallet.
Proton also provides a secure calendar app. While I use it on and off, I am not a fan of the user experience. It is not nearly as polished as the Apple Calendar app.
Apple Calendar (iCal) was created back in the Steve Jobs days, by the amazing French software artist Jean-Marie Hullot. I consider it a masterpiece in user experience. He had an eye for style and function, and we could do well as an industry to re-learn these skills.Proton take note here.
The Proton Wallet is still in beta release. No doubt it will evolve as time goes on.
What about Hardware?
I didn’t really want to get to deep into this topic in this article. I will say that I have transitioned off the iPhone and rather than settle with the Unplugged hardware, I went with a Pixel 9 Pro. I like this phone and it does what I need it to do. There is a learning curve and it is also possible to shut off a lot of the Google tracking crap.
I feel that using the Proton Suite of apps and a few other like Signal for messaging, I am making some headway to getting more control of my data. It’s not perfect, Google still has access in Android, and ultimately if you really want to limit what they can look at you should consider the GrapheneOS.
I hear from those who have done it that it’s fairly easy to install. I am sure that I’lll be experimenting with this myself. Maybe after I get out from under the current workload of projects I’m working on.
You have a choice
Whether you choose to fully transition to GrapheneOS or simply use some Proton apps, there are options available to reclaim ownership of your data.
While I sympathize that the Apple Ecosystem is very beguiling and that it can be a challenge to wean yourself from it, freedom, however, is never free; it will take some work. But I believe in my heart that you have an inalienable right to be secure in your documents, and it’s a worthy goal.





Sorry I keep forgetting to turn on comments.
Here is another link about securing Android
https://www.androidpolice.com/enhance-privacy-on-android/
I’m having my first extended experience with an android phone beyond testing, set it up for my 85 yr old dad.. I have to say, yea for hard core security it could be more secure bit it seems to me like it’s way easier to hack non-tech phone users. The store seems much less regulated for security related. I’m definitely not knowledgeable enough to make a final call but it sure seems that way so far. For me, even from just the security angle, I’m actually excited and ready to switch. I can watch to make sure I dont download the wrong thing, or click on the malicious link. For my dad, he should use an iphone.